Every extortion requires a ransom to be paid. It's the same with porn email scams.
Email scam letters can come in many different forms right into your email inbox. So you need to pay extra attention to the emails that come into your inbox or spam folder.
 |
| Photo by Nahel Abdul Hadi on Unsplash |
When you receive an email from a company you have been communicating with for so long, how do you know you are actually still exchanging correspondence with the real company? Let's use PayPal as an example.
PayPal is a legitimate online financial company that operates an online payment system which individuals and companies can use to make financial transactions. For a financial transaction to take place individuals and companies will have to open a PayPal account and register to start using it.
Once you open an account, you can send money from your PayPal account and also receive payments. When a transaction between two individuals is made, this transaction is recorded by PayPal and then you are sent an email.
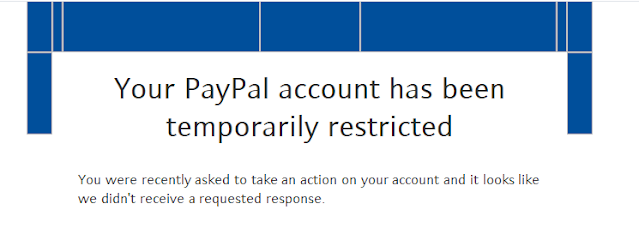
If you receive a payment for example, PayPal will send you an email telling you that you have money in your PayPal account. While all of this is a smooth running process, when scammers interfere they craft email messages to look like you are receiving an official correspondence from PayPal itself.
Everything in the eyes of someone who doesn't know will look legit. And of course, there is a link in the email which you have to click to log into your PayPal account. Here the scam is in clicking the link and inserting your login in credentials.
With your login details stolen the scammer can enter into your account and withdraw all your money. Here below is a screenshot showing a typical PayPal scam email.
The Paypal scam is just one way your hard earned money is stolen from you online. Then also there is the Bitcoin scam where you are asked to pay a ransom so photos of your naughty online habits do not get exposed on social media or circulate all over the internet.
The Bitcoin scam
With cryptocurrency use becoming a part of everyday digital life, scammers are asking for ransom payments and sending out emails to this end. Watching porn may not be your thing. But visiting porn sites is as common as watching the daily news on TV. Pornography is big business and in fact 2019 alone, Pornhub, the webs biggest site for pornography recorded 42 billion visits to its site.
This translates into an average of about 115 million site visits a day. Reviewing the past year on it's site, it says that those daily visits is,
the equivalent of the populations of Canada, Australia, Poland and the Netherlands all visiting in one day! source
This is quite a staggering number that while it is good business for Pornhub, raises the question of how much pornography is consumed online everyday. And the statistics are there for all to see. Here are just some statistics that will shock you.
a) 28,258 users are watching pornography on the internet.
b) $3,075.64 is being spent on pornography on the internet.
c) 372 people are typing the word "adult" into a search engine
d) 37 pornographic videos are created in the United States.
e) 2.5 billion emails containing porn are sent or received.
f) 68 million search queries related to pornography- 25% of total searches- are generated.
g) 16,000 queries related to child pornography are received. Source
Now Podcasts, meetings, seminars and white papers can all talk about the harmful effects pornography has on teenagers and the family/marital relationship. But there is a growing concern about how porn is frequently used by scammers,
to demand ransom from unknown people. This is the porn email scam which takes on various names such as,
porn email scam, bitcoin porn scam, sextortion emails, sextortion fishing emails.
What is a Porn email scam?
A porn email scam is one in which you are sent an email with a clear message. The email message always states why you are being contacted and for what purpose. It goes on to make demands which you have to meet.
How does it work?
Here is how a typical Bitcoin porn scam works. The scammer addresses you by telling you what they know about you in the following order,
They know the password you use, sometimes mentioning it;
They know everything about you including you email and social media contacts;
They know the porn sites you visit frequently;
That they installed a spyware which activated your webcam and recorded you in a moment of self-pleasure.
They go on to threaten you to pay some amount of money if you don't want them to expose the video on social media or to family members.
If by chance you have received an email like this, in most cases you will find it in your inbox and not in your spam folder. Here is what a typical porn scam email message looks like.
𝙸 𝚊𝚖 𝚊𝚠𝚊𝚛𝚎, xyz 𝚒𝚜 𝚢𝚘𝚞𝚛 𝚙𝚊𝚜𝚜𝚠𝚘𝚛𝚍.
𝙸 𝚛𝚎𝚚𝚞𝚒𝚛𝚎 𝚢𝚘𝚞𝚛 𝚌𝚘𝚖𝚙𝚕𝚎𝚝𝚎 𝚊𝚝𝚝𝚎𝚗𝚝𝚒𝚘𝚗 𝚏𝚘𝚛 𝚝𝚑𝚎 𝚌𝚘𝚖𝚒𝚗𝚐 𝚃𝚠𝚎𝚗𝚝𝚢-𝚏𝚘𝚞𝚛 𝚑𝚛𝚜, 𝚘𝚛 𝙸 𝚖𝚊𝚢 𝚖𝚊𝚔𝚎 𝚜𝚞𝚛𝚎 𝚢𝚘𝚞 𝚝𝚑𝚊𝚝 𝚢𝚘𝚞 𝚕𝚒𝚟𝚎 𝚘𝚞𝚝 𝚘𝚏 𝚜𝚑𝚊𝚖𝚎 𝚏𝚘𝚛 𝚝𝚑𝚎 𝚛𝚎𝚜𝚝 𝚘𝚏 𝚢𝚘𝚞𝚛 𝚎𝚡𝚒𝚜𝚝𝚎𝚗𝚌𝚎.
𝙷𝚎𝚕𝚕𝚘 𝚝𝚑𝚎𝚛𝚎, 𝚢𝚘𝚞 𝚍𝚘𝚗'𝚝 𝚔𝚗𝚘𝚠 𝚖𝚎. 𝙷𝚘𝚠𝚎𝚟𝚎𝚛 𝙸 𝚔𝚗𝚘𝚠 𝚓𝚞𝚜𝚝 𝚊𝚋𝚘𝚞𝚝 𝚎𝚟𝚎𝚛𝚢𝚝𝚑𝚒𝚗𝚐 𝚛𝚎𝚐𝚊𝚛𝚍𝚒𝚗𝚐 𝚢𝚘𝚞. 𝙰𝚕𝚕 𝚘𝚏 𝚢𝚘𝚞𝚛 𝚏𝚊𝚌𝚎𝚋𝚘𝚘𝚔 𝚌𝚘𝚗𝚝𝚊𝚌𝚝 𝚕𝚒𝚜𝚝, 𝚖𝚘𝚋𝚒𝚕𝚎 𝚙𝚑𝚘𝚗𝚎 𝚌𝚘𝚗𝚝𝚊𝚌𝚝𝚜 𝚊𝚗𝚍 𝚊𝚕𝚕 𝚝𝚑𝚎 𝚍𝚒𝚐𝚒𝚝𝚊𝚕 𝚊𝚌𝚝𝚒𝚟𝚒𝚝𝚢 𝚘𝚗 𝚢𝚘𝚞𝚛 𝚌𝚘𝚖𝚙𝚞𝚝𝚎𝚛 𝚏𝚛𝚘𝚖 𝚙𝚛𝚎𝚟𝚒𝚘𝚞𝚜 𝟷𝟷𝟽 𝚍𝚊𝚢𝚜.
𝙸𝚗𝚌𝚕𝚞𝚍𝚒𝚗𝚐, 𝚢𝚘𝚞𝚛 𝚜𝚎𝚕𝚏 𝚙𝚕𝚎𝚊𝚜𝚞𝚛𝚎 𝚟𝚒𝚍𝚎𝚘 𝚏𝚘𝚘𝚝𝚊𝚐𝚎, 𝚠𝚑𝚒𝚌𝚑 𝚋𝚛𝚒𝚗𝚐𝚜 𝚖𝚎 𝚝𝚘 𝚝𝚑𝚎 𝚖𝚊𝚒𝚗 𝚖𝚘𝚝𝚒𝚟𝚎 𝚠𝚑𝚢 𝙸 '𝚖 𝚌𝚘𝚖𝚙𝚘𝚜𝚒𝚗𝚐 𝚝𝚑𝚒𝚜 𝚜𝚙𝚎𝚌𝚒𝚏𝚒𝚌 𝚎-𝚖𝚊𝚒𝚕 𝚝𝚘 𝚢𝚘𝚞.
𝚆𝚎𝚕𝚕 𝚝𝚑𝚎 𝚙𝚛𝚎𝚟𝚒𝚘𝚞𝚜 𝚝𝚒𝚖𝚎 𝚢𝚘𝚞 𝚠𝚎𝚗𝚝 𝚝𝚘 𝚝𝚑𝚎 𝚊𝚍𝚞𝚕𝚝 𝚖𝚊𝚝𝚎𝚛𝚒𝚊𝚕 𝚘𝚗𝚕𝚒𝚗𝚎 𝚜𝚒𝚝𝚎𝚜, 𝚖𝚢 𝚜𝚙𝚢𝚠𝚊𝚛𝚎 𝚎𝚗𝚍𝚎𝚍 𝚞𝚙 𝚋𝚎𝚒𝚗𝚐 𝚊𝚌𝚝𝚒𝚟𝚊𝚝𝚎𝚍 𝚒𝚗𝚜𝚒𝚍𝚎 𝚢𝚘𝚞𝚛 𝚌𝚘𝚖𝚙𝚞𝚝𝚎𝚛 𝚠𝚑𝚒𝚌𝚑 𝚎𝚗𝚍𝚎𝚍 𝚞𝚙 𝚍𝚘𝚌𝚞𝚖𝚎𝚗𝚝𝚒𝚗𝚐 𝚊 𝚎𝚢𝚎-𝚌𝚊𝚝𝚌𝚑𝚒𝚗𝚐 𝚏𝚘𝚘𝚝𝚊𝚐𝚎 𝚘𝚏 𝚢𝚘𝚞𝚛 𝚖𝚊𝚜𝚝𝚞𝚛𝚋𝚊𝚝𝚒𝚘𝚗 𝚊𝚌𝚝 𝚋𝚢 𝚝𝚛𝚒𝚐𝚐𝚎𝚛𝚒𝚗𝚐 𝚢𝚘𝚞𝚛 𝚠𝚎𝚋 𝚌𝚊𝚖𝚎𝚛𝚊.
(𝚢𝚘𝚞 𝚐𝚘𝚝 𝚊 𝚜𝚎𝚛𝚒𝚘𝚞𝚜𝚕𝚢 𝚞𝚗𝚞𝚜𝚞𝚊𝚕 𝚙𝚛𝚎𝚏𝚎𝚛𝚎𝚗𝚌𝚎 𝚋𝚝𝚠 𝚑𝚊𝚑𝚊)
𝙸 𝚑𝚊𝚟𝚎 𝚝𝚑𝚎 𝚌𝚘𝚖𝚙𝚕𝚎𝚝𝚎 𝚛𝚎𝚌𝚘𝚛𝚍𝚒𝚗𝚐. 𝙹𝚞𝚜𝚝 𝚒𝚗 𝚌𝚊𝚜𝚎 𝚢𝚘𝚞 𝚝𝚑𝚒𝚗𝚔 𝙸 𝚊𝚖 𝚏𝚘𝚘𝚕𝚒𝚗𝚐 𝚊𝚛𝚘𝚞𝚗𝚍, 𝚓𝚞𝚜𝚝 𝚛𝚎𝚙𝚕𝚢 𝚙𝚛𝚘𝚘𝚏 𝚊𝚗𝚍 𝙸 𝚠𝚒𝚕𝚕 𝚋𝚎 𝚏𝚘𝚛𝚠𝚊𝚛𝚍𝚒𝚗𝚐 𝚝𝚑𝚎 𝚛𝚎𝚌𝚘𝚛𝚍𝚒𝚗𝚐 𝚛𝚊𝚗𝚍𝚘𝚖𝚕𝚢 𝚝𝚘 𝟹 𝚙𝚎𝚘𝚙𝚕𝚎 𝚢𝚘𝚞 𝚔𝚗𝚘𝚠.
𝙸𝚝 𝚌𝚘𝚞𝚕𝚍 𝚎𝚗𝚍 𝚞𝚙 𝚋𝚎𝚒𝚗𝚐 𝚢𝚘𝚞𝚛 𝚏𝚛𝚒𝚎𝚗𝚍𝚜, 𝚌𝚘 𝚠𝚘𝚛𝚔𝚎𝚛𝚜, 𝚋𝚘𝚜𝚜, 𝚖𝚘𝚝𝚑𝚎𝚛 𝚊𝚗𝚍 𝚏𝚊𝚝𝚑𝚎𝚛 (𝙸 𝚍𝚘𝚗'𝚝 𝚔𝚗𝚘𝚠! 𝙼𝚢 𝚜𝚢𝚜𝚝𝚎𝚖 𝚠𝚒𝚕𝚕 𝚛𝚊𝚗𝚍𝚘𝚖𝚕𝚢 𝚜𝚎𝚕𝚎𝚌𝚝 𝚝𝚑𝚎 𝚌𝚘𝚗𝚝𝚊𝚌𝚝𝚜).
𝚆𝚘𝚞𝚕𝚍 𝚢𝚘𝚞 𝚋𝚎 𝚊𝚋𝚕𝚎 𝚝𝚘 𝚕𝚘𝚘𝚔 𝚒𝚗𝚝𝚘 𝚊𝚗𝚢𝚘𝚗𝚎'𝚜 𝚎𝚢𝚎𝚜 𝚊𝚐𝚊𝚒𝚗 𝚊𝚏𝚝𝚎𝚛 𝚒𝚝? 𝙸 𝚚𝚞𝚎𝚜𝚝𝚒𝚘𝚗 𝚝𝚑𝚊𝚝...
𝙽𝚘𝚗𝚎𝚝𝚑𝚎𝚕𝚎𝚜𝚜, 𝚒𝚝 𝚍𝚘𝚎𝚜 𝚗𝚘𝚝 𝚑𝚊𝚟𝚎 𝚝𝚘 𝚋𝚎 𝚝𝚑𝚊𝚝 𝚛𝚘𝚞𝚝𝚎.
𝙸 𝚠𝚘𝚞𝚕𝚍 𝚕𝚒𝚔𝚎 𝚝𝚘 𝚖𝚊𝚔𝚎 𝚢𝚘𝚞 𝚊 𝚘𝚗𝚎 𝚝𝚒𝚖𝚎, 𝚗𝚘𝚗 𝚗𝚎𝚐𝚘𝚝𝚒𝚊𝚋𝚕𝚎 𝚘𝚏𝚏𝚎𝚛.
𝙶𝚎𝚝 $ 𝟸𝟶𝟶𝟶 𝚒𝚗 𝚋𝚒𝚝𝚌𝚘𝚒𝚗 𝚊𝚗𝚍 𝚜𝚎𝚗𝚍 𝚒𝚝 𝚘𝚗 𝚝𝚑𝚎 𝚋𝚎𝚕𝚘𝚠 𝚊𝚍𝚍𝚛𝚎𝚜𝚜:
xvxvxvxvxvxhjnkkksllsllsllsaj
(𝙸𝚏 𝚢𝚘𝚞 𝚍𝚘 𝚗𝚘𝚝 𝚔𝚗𝚘𝚠 𝚑𝚘𝚠, 𝚕𝚘𝚘𝚔𝚞𝚙 𝚑𝚘𝚠 𝚝𝚘 𝚙𝚞𝚛𝚌𝚑𝚊𝚜𝚎 𝚋𝚒𝚝𝚌𝚘𝚒𝚗. 𝙳𝚘 𝚗𝚘𝚝 𝚠𝚊𝚜𝚝𝚎 𝚖𝚢 𝚒𝚖𝚙𝚘𝚛𝚝𝚊𝚗𝚝 𝚝𝚒𝚖𝚎)
𝙸𝚏 𝚢𝚘𝚞 𝚜𝚎𝚗𝚍 𝚝𝚑𝚒𝚜 '𝚍𝚘𝚗𝚊𝚝𝚒𝚘𝚗' (𝚕𝚎𝚝'𝚜 𝚌𝚊𝚕𝚕 𝚒𝚝 𝚝𝚑𝚊𝚝?). 𝙰𝚏𝚝𝚎𝚛 𝚝𝚑𝚊𝚝, 𝙸 𝚠𝚒𝚕𝚕 𝚐𝚘 𝚊𝚠𝚊𝚢 𝚊𝚗𝚍 𝚗𝚎𝚟𝚎𝚛 𝚌𝚘𝚗𝚝𝚊𝚌𝚝 𝚢𝚘𝚞 𝚊𝚐𝚊𝚒𝚗. 𝙸 𝚠𝚒𝚕𝚕 𝚛𝚎𝚖𝚘𝚟𝚎 𝚎𝚟𝚎𝚛𝚢𝚝𝚑𝚒𝚗𝚐 𝙸'𝚟𝚎 𝚐𝚘𝚝 𝚊𝚋𝚘𝚞𝚝 𝚢𝚘𝚞. 𝚈𝚘𝚞 𝚖𝚊𝚢 𝚟𝚎𝚛𝚢 𝚠𝚎𝚕𝚕 𝚔𝚎𝚎𝚙 𝚘𝚗 𝚕𝚒𝚟𝚒𝚗𝚐 𝚢𝚘𝚞𝚛 𝚘𝚛𝚍𝚒𝚗𝚊𝚛𝚢 𝚍𝚊𝚢 𝚝𝚘 𝚍𝚊𝚢 𝚕𝚒𝚏𝚎𝚜𝚝𝚢𝚕𝚎 𝚠𝚒𝚝𝚑 𝚣𝚎𝚛𝚘 𝚌𝚘𝚗𝚌𝚎𝚛𝚗𝚜.
𝚈𝚘𝚞 𝚑𝚊𝚟𝚎 𝚐𝚘𝚝 𝟷 𝚍𝚊𝚢 𝚝𝚘 𝚍𝚘 𝚜𝚘. 𝚈𝚘𝚞𝚛 𝚝𝚒𝚖𝚎 𝚜𝚝𝚊𝚛𝚝𝚜 𝚘𝚏𝚏 𝚊𝚜 𝚜𝚘𝚘𝚗 𝚢𝚘𝚞 𝚛𝚎𝚊𝚍 𝚝𝚑𝚒𝚜 𝚖𝚊𝚒𝚕. 𝙸 𝚑𝚊𝚟𝚎 𝚐𝚘𝚝 𝚊𝚗 𝚘𝚗𝚎 𝚘𝚏 𝚊 𝚔𝚒𝚗𝚍 𝚌𝚘𝚍𝚎 𝚝𝚑𝚊𝚝 𝚠𝚒𝚕𝚕 𝚝𝚎𝚕𝚕 𝚖𝚎 𝚘𝚗𝚌𝚎 𝚢𝚘𝚞 𝚜𝚎𝚎 𝚝𝚑𝚒𝚜 𝚎-𝚖𝚊𝚒𝚕 𝚜𝚘 𝚍𝚘𝚗'𝚝 𝚊𝚝𝚝𝚎𝚖𝚙𝚝 𝚝𝚘 𝚙𝚕𝚊𝚢 𝚜𝚖𝚊𝚛𝚝.
What are the effects of a sextortion email
Receiving an email like this is always threatening and will get many people checking their conscious. Here is how it works on an email recipient,
Password
There is a clear indication of a password that you have used before or are currently using. This gives you the idea that the sender knows a lot about you.
Spyware
Having spyware in your computer means that your computer has been infiltrated by an unwanted software that is stealing your data and sensitive information. You have been hacked!
Video footage
You may have been watching porn in the quiet of your home. Reading this mail may have got you thinking of the last time you visited a porn site and excited as you were,
worked yourself away into masturbation.
When you add everything up, here is what you get. The password corresponds to a password you might be currently using. And so you think that if the scammer knows your password, then they already have access to your sensitive data.
And if they have activated a spyware then the spyware is working in the background,
And if they have activated a spyware then the spyware is working in the background,
and has actually recorded you while you were watching porn and pleasing yourself.
If you are guilty of such acts, the fear of being exposed grips you. You'd want to save your reputation and quickly pay the scammers. Payment is usually in Bitcoins and is picked up anonymously by the scammer.
Symantec in 2019 blocked almost 300 million extortion scam emails between the months of January and may, 2019. This shows how the scam is widespread and on the increase.
Symantec in 2019 blocked almost 300 million extortion scam emails between the months of January and may, 2019. This shows how the scam is widespread and on the increase.
Why you are tricked
Are you guilty of such acts of self-pleasure in front of a webcam? Do you fear your actions might be recorded and eventually exposed? Well if you are guilty and fear your spouse or family getting to know about it,
then this will force you to decide to take action and pay.
But here is the thing, much of the claims of being recorded, and that recording being exposed is bogus. It is only meant to scare you as this article,
then this will force you to decide to take action and pay.
But here is the thing, much of the claims of being recorded, and that recording being exposed is bogus. It is only meant to scare you as this article,
Sextortion emails and porn scams are back-don't let them scare you! on the nakesecurity.sophos.com website reveals.
According to the article the bogus claim is only made to scare you into believing they have a recording. But it goes on to say that,
if the crooks really wanted to convince you they had such a video, they'd put a still frame or a short clip from it in the sextortion email.
But the scammers only include a password you have used and which they probably got from a data breach.
if the crooks really wanted to convince you they had such a video, they'd put a still frame or a short clip from it in the sextortion email.
But the scammers only include a password you have used and which they probably got from a data breach.
What to do against porn scam emails.
The rise in porn scam email is alarming and this calls for increased awareness when it comes to your online security. You are a target the moment you receive such an email.
And if you are afraid of the outcome, perhaps because you are guilty,
you may find indulging in paying the scammers a good idea.
But there's no need to panic, and no need to fear being exposed. All the scammers want is your money. And so if you have received a porn scam email here are some of the things you can do to prevent from falling for the scam.
1) Delete the email immediately. Do not think twice before doing so.
2) Change your password if you are still using an account with the mentioned password.
3) If there are links in the mail do not click on the links
4) Never pay the ransom.
Final consideration
With the amount of email messages that flood people's email accounts, you are more likely to receive a few of these emails messages every now and then. They may fall into your inbox sometimes instead of your spam folder. Wherever they fall, do not open them but delete them immediately.
If you have a contacts list in your email account, you may to inform them about it so they can be aware. this way you can save a lot of people from getting scammed.
Naked Security,Sophos
Symantec

No comments:
Post a Comment